Tired of juggling accounts and passwords just to get through your daily online tasks? Wary of surrendering your data to tech giants in exchange for the convenience of “login with Facebook, Google, or Apple”? You’re not alone. Managing our digital identities has been a challenge, since the early days of the internet.
The good news is, a change is coming. A new approach to sharing, storing, and verifying data is emerging, and it promises to fill a massive gap in the internet as we know it today — its identity layer. It’s called SSI, short for self-sovereign identity.
With SSI, you control your data, deciding what information to share and with whom. No more endless accounts and passwords! No more entrusting your data to corporations. No more risk of data breaches and leaks.
But that’s just the beginning. SSI has the potential to benefit not just individuals, but also companies and institutions by streamlining processes, reducing fraud, and fostering a more secure online environment. In this article, we dive deeper into this innovative concept and discover how SSI can transform digital interactions.
What is Self-Sovereign Identity (SSI)?
Self-Sovereign Identity (SSI) is a concept in digital identity, where individuals have complete ownership and control over their personal identity information. Unlike traditional identity systems that rely on centralized authorities or third-party intermediaries, SSI empowers users to manage, and share, their data autonomously. This approach ensures that individuals can authenticate themselves and prove their identity without depending on external entities, enhancing privacy, security, and user autonomy.
In an SSI framework, identity data is stored privately, in users’ digital wallets, and protected from unauthorized access thanks to the power of cryptography and decentralization. Users control access to their information, enabling them to grant or revoke permissions to various service providers or entities as needed. This user-centric model stands in contrast to traditional models, where identity data is often stored in centralized databases vulnerable to breaches and misuse.
Key Features and Principles of SSI
Here are the key features and principles of SSI:
- User-Centric: In SSI, users have access and control over their identity data. They can decide what information to share, with whom, and for how long.
- Privacy-Enhancing: SSI is designed to prioritize privacy. SSI uses technologies like blockchain to allow users to prove their identity without revealing unnecessary personal information. Disclosure of claims must be minimized.
- Decentralized: Traditional identity systems are controlled by central authorities, while SSI is built on decentralized principles. The holder keeps all his data within the wallet.
- Interoperable: SSI systems aim to be universally applicable, allowing users to use their identity across different services and platforms without separate credentials.
- Secure: These systems use advanced cryptographic techniques to ensure that identity data is secure and cannot be tampered with.
- Consent-Based: Any sharing of personal data in SSI systems is based on the user’s explicit consent, providing greater control over personal data.
- Portable: Users can carry their identity across different platforms and services without depending on a single provider.
- Transparent: System and algorithms are transparent so that other entities can verify.
Empe Insight
“One of the key advantages of SSI technology is its interoperability. This means that the Holder can store credentials from different issuers, using various DID methods. On the other hand, the Verifier can verify these credentials in different registries. This makes SSI an extremely flexible solution that can be widely adopted across various business sectors.”
Łukasz Jankowski, Solutions Architect, Empeiria
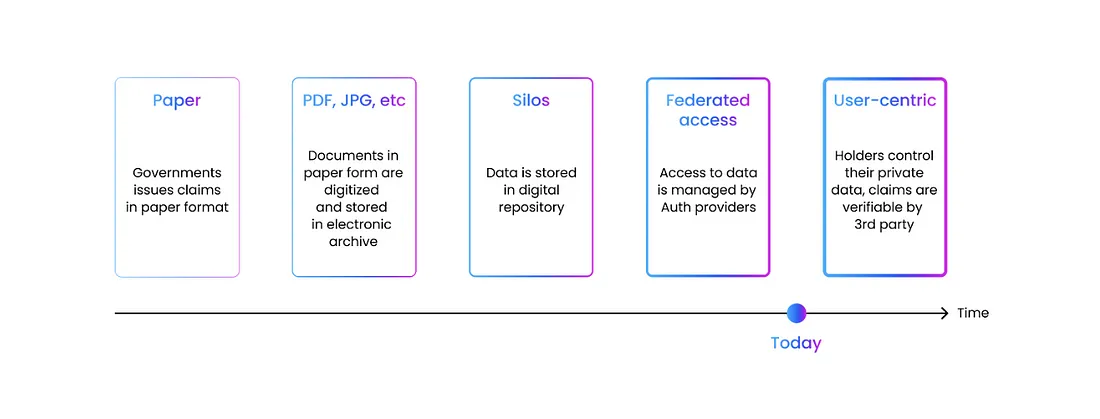
Before SSI
SSI didn’t appear out of nowhere. Instead, a series of steps in the evolution of digital identity management led to this invention. We currently identify the following stages of this evolution:
- Paper Era Credential Issuance: In the pre-internet era, identity credentials were issued in paper form, hand-signed and sealed by officials (issuer), and handed over in paper form to the applicant (holder). The post office could handle this operation.
- Digitalization and Electronic Storage: With the advent of digitalization, we began scanning and storing data electronically as graphic files or PDFs. This facilitated the search and archiving of documents but left unresolved issues of distribution and verification outside the office. The electronic transmission of credentials to applicants allowed them to present them as needed, but verifying the authenticity of such documents, especially those of critical importance like property deeds or identity proofs, was problematic.
- Silos Model: The centralization of electronic data repositories was a significant advancement. It granted applicants remote access to necessary documents after logging in with authentication data.
- Federated Login Model: In the Silos Model, the need to memorize access data for various systems and cope with diverse authentication methods posed a challenge. One solution that emerged to address it is the Federated Login Model, exemplified by OpenID, commonly recognized as “Login with Google” or “Login with Facebook.”
- User-Centric Model: While the Federated Login Model enhanced accessibility, it failed to resolve two crucial challenges: credentials storage and verification. Enter Self-Sovereign Identity (SSI), a User-Centric Model, heralding a paradigm shift that addresses these challenges and signifies a transformative leap toward a more secure and user-centric digital identity landscape.

Technical Foundations of SSI
Self-Sovereign Identity (SSI) relies on a blend of innovative technologies to empower user control and decentralize identity management. Here’s a breakdown of the key innovations that make self-sovereign identity possible:
- Blockchain Technology: Blockchain plays a crucial role in SSI. It provides a tamper-proof ledger for recording critical events like the issuance and ownership of Verifiable Credentials (VCs). Imagine a public registry where everyone can verify the authenticity of a credential without relying on a central authority. Transactions on the blockchain are secured through cryptography, making it highly resistant to tampering or fraud.
- Public-Key Cryptography: This creates a key pair — a public key for sharing information and a private key for secure access. VCs are typically signed with the issuer’s private key, and anyone can verify the signature using the corresponding public key. This ensures the authenticity of the credential.
- Digital Signatures: Similar to signing a physical document, digital signatures provide cryptographic proof that a specific entity (e.g., university) issued a VC. This allows relying parties (e.g., employers) to trust the information without contacting the issuer directly.
- Hash Functions: These are one-way mathematical functions that transform data into a unique fingerprint. Any change to the data will result in a completely different hash, making it easy to detect alterations. Hash functions are used to ensure the data within a VC hasn’t been tampered with.
- Decentralized Identifiers (DIDs): Imagine a unique web address for your identity, not tied to any specific platform or service provider. DIDs provide this functionality. They are globally unique, user-managed identifiers, offering greater control over how their identity is represented online.
- Verifiable Credentials (VCs): These are tamper-proof digital documents containing a user’s verifiable claims about themselves, such as educational qualifications or work experience. VCs are issued by trusted entities (e.g., universities) and stored securely in the user’s digital wallet. When needed, users can selectively share specific VCs with third parties for verification. Cryptographic proofs are used to demonstrate the validity and authenticity of the credential without revealing any unnecessary underlying data.
This combination of technologies empowers users to control their identity data, securely share verified credentials, and interact online with greater trust and transparency.
Roles in the SSI framework
The most convenient way to depict the SSI framework participants is via the so-called SSI Triangle. Below is just a brief introduction of the core participants:
- Issuers: Trusted entities authorized to issue VCs. This could include universities issuing diplomas, governments providing licenses, or employers verifying employment status, etc.
- Holders: Individuals or entities who own their DIDs and VCs stored securely in their digital wallets.
- Verifiers: Parties who rely on VCs to confirm an identity claim. This could be an employer verifying work experience for a job application or a bank verifying age for opening an account.

SSI Protocols and Standards
The success of SSI relies on a strong foundation of interoperable protocols and standards. Here, we explore some key contributions:
- W3C DID Standard: The World Wide Web Consortium (W3C) plays a crucial role in defining core standards for SSI. The W3C Decentralized Identifier (DID) standard specifies how to create and manage globally unique identifiers that are independent of any centralized authority. This empowers users to control their DIDs and decide where their identity data resides. Imagine a universal username you control, not tied to a specific platform!
- W3C Verifiable Credentials Data Model: This W3C standard defines the structure and format for Verifiable Credentials (VCs). It specifies what information a VC can contain, how it should be formatted, and how it can be cryptographically signed for tamper-proof verification. This standardization ensures that VCs issued by different entities can be understood and verified consistently across the SSI ecosystem.
- Industry Initiatives and Working Groups: Beyond W3C, numerous industry initiatives and working groups are actively shaping the future of SSI standards. These groups bring together stakeholders like technology providers, government agencies, and user representatives to develop and implement best practices for SSI deployments. Examples include the Decentralized Identity Foundation (DIF) and the Identity Foundation (IDF). Their ongoing work fosters interoperability, promotes innovation, and ensures a robust and user-centric SSI ecosystem.
Implementation and Use Cases
SSI is no longer a theoretical concept; it’s gaining traction across various sectors. Let’s explore some potential real-world applications:
Individual Digital Identity Management:
- Secure Logins: Imagine logging into online services without usernames and passwords. SSI enables users to present verifiable credentials (e.g., age verification) to access age-restricted content without revealing unnecessary personal information.
- Decentralized Wallets: Digital wallets for storing and managing DIDs and VCs are actively being developed. These wallets empower individuals to control their data and decide what information to share with different service providers.
Enterprise and Institutional Solutions:
- Customer Onboarding: Streamline customer onboarding processes by allowing users to share pre-verified credentials (e.g., proof of address) from trusted issuers, eliminating the need for repetitive data collection.
- Supply Chain Management: Verify the authenticity of products and track their origin through the supply chain using tamper-proof VCs. This enhances transparency and combats counterfeiting.
Travel and Immigration: Imagine a future where travelers can present verifiable credentials for passports or visas at border crossings, simplifying the process and reducing reliance on physical documents. - Academic Credentials: Universities can issue verifiable credentials for diplomas or transcripts, allowing students to easily share them with potential employers or educational institutions globally.
These are just a few examples, and the potential applications of SSI are vast. As the technology matures and adoption increases, we can expect even more innovative use cases to emerge, transforming how we manage and interact with our digital identities online.
Empe Insight:
“SSI technology finds wide application in many businesses, from finance and healthcare to education and logistics, to name a few. Thanks to the ability to securely and privately store and share data, including the most critical ones, as well as revoke them, it can be utilized in many use cases across various industries.”
Łukasz Jankowski, Solutions Architect, Empeiria
Regulatory and Compliance Aspects
The world of data privacy is constantly evolving, with regulations like the General Data Protection Regulation (GDPR) placing stricter controls on how personal information is collected, used, and stored. Here’s how SSI interacts with this regulatory landscape:
Alignment with Data Privacy Regulations: SSI and data privacy regulations like GDPR share a common goal: empowering individuals to control their data. SSI principles align perfectly with GDPR requirements. By putting users in control of their data through DIDs and VCs, SSI facilitates compliance by making it easier for individuals to access, share, and revoke their information.
SSI offers unique advantages for regulatory compliance. Here’s how:
- Transparency: Verifiable Credentials provide a transparent record of who issued the data, what information it contains, and with whom it was shared. This granular control allows users to understand how their data is being used.
- User Control: By giving users control over their data through DIDs and digital wallets, SSI empowers them to comply with “Right to be Forgotten” requests or easily revoke access to their information. This reduces the burden on organizations to manage individual data requests.
Overall, SSI presents a promising solution for navigating the complexities of data privacy regulations. As the technology matures and regulations evolve, a more user-centric and compliant approach to data management can be achieved.
Empeiria’s EVDI and SSI
Empeiria’s End-to-End Verifiable Data Infrastructure (EVDI) seamlessly bridges legacy data systems with decentralized SSI solutions, enabling a smooth transition to modern verifiable data management. With one-click deployment, organizations can easily adopt decentralized data ecosystems, enhancing security, privacy, and efficiency.
Conclusion
The potential of SSI to transform our digital interaction is undeniable. It enables a future where individuals own their digital identities, share information securely, and experience a more user-centric online environment.
This transformation requires active participation from all stakeholders. Individuals can embrace SSI by learning about the technology and demanding control over their data. Businesses and institutions can explore how SSI can streamline processes, enhance security, and build trust. Policymakers can collaborate with industry to develop regulations that promote innovation while safeguarding privacy.
As we work towards a future powered by SSI, let’s remember that the key to unlocking the full potential of the digital world lies in empowering individuals to control their own identities.
Get in touch
For inquiries or further information, contact Empeiria at [email protected], on Twitter/X, or LinkedIn. Follow Empeiria on social media for the latest news & updates.